The Matrix V Integrated Security Management System (ISMS) is ELID’s premier Software & Security Management System designed to meet advanced security needs, suited for corporate & government security market.
Matrix V System is designed for professional and serious security enforcement managers who demand high performance, accountability and consolidated situational crisis management. It uses state-of-the-art, multi-purpose, IP Controllers with intuitive user reader interface devices and Integrated Software modules to build a comprehensive Integrated Security Management System.
With its extensive capability to support 8000 access portals, with 144,000 inputs and 280,000 outputs (for I/O monitoring), Matrix V’s broad system capabilities make it suitable for global deployment, across countries and regions, in the most demanding security requirements.
Matrix V is the most comprehensive Total Integrated Solution System in its class. It combines all facets of Security Management with all human interface management applications on a single platform in a single software package. A total of 8000 access portals/ 16,000 readers with 128,000 inputs and 256,000 outputs can be monitored and control on a this singular platform.
- 18 Modules ….and still expanding
- Door Access Management
- Intrusion Alarm Monitoring
- Lift Access Control
- Vehicle Access Control
- Lobby/ Visitor Management
- CCTV
| Door Access Management |
 Maintain total control and surveillance of all door access in your secure areas directly from any of the unlimited client workstations. All door access activity is transmitted directly to your computer screen. You can also give specific commands to doors such as opening and closing them directly, sealing them off from further access, etc. Maintain total control and surveillance of all door access in your secure areas directly from any of the unlimited client workstations. All door access activity is transmitted directly to your computer screen. You can also give specific commands to doors such as opening and closing them directly, sealing them off from further access, etc. |
| Features include: |
| Anti-Passback Options - Anti-Passback enforces users who enter a secure area with a card to leave the area before the card may be used to enter that secure area again. |
| Inhibit Access and Permanent Lock Release - Permanently lock and unlock particular doors instantly on demand in response to specific events such as escaping thief or a fire that demands immediate evacuation. |
| Special door configurations such as dual card mode, where in order to access a door, a higher level ''escort'' card is required, and interlock configuration, where one has to enter close one door before another door ahead will be unlocked. |
| Mixed Mode Capability |
| The same keypad reader used for Door Access can be utilised as a Time Attendance & Reasoning Terminal. For every Late In, Early Out clockings, up to 20 reasoning code labels can be displayed on the keypad LCD and selected by Users. This enables Human Resources to enable users to seolf justify reasons for his or her tardiness. |
| Lift Access Control |
 Lift Access may be restricted according to the access rights of a partcular lift access cardholder to access particular floors. Unauthorized floor entry is restricted at the lift car level, as restricted floors buttons will be rendered inoprative. In addition, floor call overriding can be enabled to give lift usage priority to very important persons (VIP)such as Executive Officers, visiting dignitaries, etc. Lift Access may be restricted according to the access rights of a partcular lift access cardholder to access particular floors. Unauthorized floor entry is restricted at the lift car level, as restricted floors buttons will be rendered inoprative. In addition, floor call overriding can be enabled to give lift usage priority to very important persons (VIP)such as Executive Officers, visiting dignitaries, etc. |
| REO Vision II Network Video Recording |
 REO Vision II is an ELID's PC-based Network Video Recording System (NVR) that provides for comprehensive surveillance with real time monitoring functions - a seamless integrated solution of surveillance technology with Matrix V system. REO Vision II is an ELID's PC-based Network Video Recording System (NVR) that provides for comprehensive surveillance with real time monitoring functions - a seamless integrated solution of surveillance technology with Matrix V system. |
| Car Park Access Control |
 Control access to a car park through the use of User ID Cards at the car park gantry areas. Matrix V User and Visitor Cards can be used to gain access to car park gantries. Anti-passback applies to vehicles as well - once a card has been used for entry. I t can only be used to exit. This is to prevent multiple vehicles from using the same card to enter the car park area. Control access to a car park through the use of User ID Cards at the car park gantry areas. Matrix V User and Visitor Cards can be used to gain access to car park gantries. Anti-passback applies to vehicles as well - once a card has been used for entry. I t can only be used to exit. This is to prevent multiple vehicles from using the same card to enter the car park area. |
| Monitor vehicle traffic and directly control the gantry from the client workstation. |
|
|
| Detect & Alert |
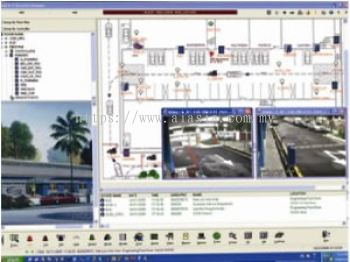
 Receive alert messages regarding security breaches on your security system, such as unauthorized intrusions or device tempering, as well as a map of the immedite vicinity of the alert highlighting the location (s) of the accurrences directly on your computer screen in real time as they accur. This helps you response time and assists you in organizing and implementing a response such as contacting the police or deploying security personnel to the scene. Receive alert messages regarding security breaches on your security system, such as unauthorized intrusions or device tempering, as well as a map of the immedite vicinity of the alert highlighting the location (s) of the accurrences directly on your computer screen in real time as they accur. This helps you response time and assists you in organizing and implementing a response such as contacting the police or deploying security personnel to the scene. |
| Interlogix |
 The interlogix engine enables 3rd party systems to be integrated to Matrix V to become a total integrated knowledge solution by implementing any of the following methods; The interlogix engine enables 3rd party systems to be integrated to Matrix V to become a total integrated knowledge solution by implementing any of the following methods; |
|
|
|
| Enterprise |
 Matrix V Enterprise supports centralised online monitoring of an established group of Matrix V sites. A system user will be able to log into any selected linked Matrix V database sites via an authorized login to centrally monitor online transaction, and this include selective alarms. Matrix V Enterprise supports centralised online monitoring of an established group of Matrix V sites. A system user will be able to log into any selected linked Matrix V database sites via an authorized login to centrally monitor online transaction, and this include selective alarms. |
| For convenience, it provides both basic card database manage ment and reporting which can also be saved in preferred format such as QuickReport format (.QRP), text format (.TXT), Excel format (.CSV), or HTML. |
| Visitor Manager |
 Manage a large volume of visitor traffic through your premise quickly, easily and accurately. Manage a large volume of visitor traffic through your premise quickly, easily and accurately. |
|
|
|
|
|
| Mobile Alert E-mail |
 This is useful for passive tracing or monitoring purposes. It allows registered personnel(s) to receive alert messages in the form of an email whenever a pre-determined alarm/activities occurs within the boundary of the Matrix V system. It supports scheduled reporting whereby reportsettings can be pre-defined, and correspondingly sent to registered personnel(s) according to defined schedules. This is useful for passive tracing or monitoring purposes. It allows registered personnel(s) to receive alert messages in the form of an email whenever a pre-determined alarm/activities occurs within the boundary of the Matrix V system. It supports scheduled reporting whereby reportsettings can be pre-defined, and correspondingly sent to registered personnel(s) according to defined schedules. |
| Unlimited Matrix V users can be registered into the module with valid email addresese and they can be categorized individually or as group. |
| Broadcast Manager |
 Allows brief messages to be left for particular cardholders as they access card reader points. The message is displayed on the accessed card reader's LED/LCD display upon the recipient(s) swiping his/her card on the card reader. This system is similar to the Short Message Service (SMS) used with mobile phones and can be very useful alternative method for the proliferation of urgent short messages to one or a number of personnel within a large building quickly. Allows brief messages to be left for particular cardholders as they access card reader points. The message is displayed on the accessed card reader's LED/LCD display upon the recipient(s) swiping his/her card on the card reader. This system is similar to the Short Message Service (SMS) used with mobile phones and can be very useful alternative method for the proliferation of urgent short messages to one or a number of personnel within a large building quickly. |
| Web Matrix II |
 Web Matrix II allows authorized users to log on to the Matrix V systems via the internet. These users are able to access to the system, operating at basic level from anywhere in the world. The basic operations include alarm monitoring functions and generation of reports. Web Matrix II allows authorized users to log on to the Matrix V systems via the internet. These users are able to access to the system, operating at basic level from anywhere in the world. The basic operations include alarm monitoring functions and generation of reports. |
| Time Track |
 Users coming and going from work have their access times logged at the card reader entrances and exits of their work areas. This enables human resource personnel to notice personnel access behavior such as promptness, tardiness, early out, overtime, absenteeism, lengthy breaks, incomplete entries (i.e. an out entry but no in-entry, an in-entry but no out-entry), abnormal permissible movement (i.e. a person from Accounting and Finance in the R&D Department, etc.). Users coming and going from work have their access times logged at the card reader entrances and exits of their work areas. This enables human resource personnel to notice personnel access behavior such as promptness, tardiness, early out, overtime, absenteeism, lengthy breaks, incomplete entries (i.e. an out entry but no in-entry, an in-entry but no out-entry), abnormal permissible movement (i.e. a person from Accounting and Finance in the R&D Department, etc.). |
| Guard & Patrol |
 Guard Touring is an additional security feature involving the close monitoring of guard patrol movement through their assigned routes in security areas. During a Guard Tour, patrolling guards swipe their Guard Tour cards at specific card readers along their tour, which register on the security interface. Each Guard Tour has a strict schedule, with a list of periods during which the patrolling guard must swipe the Guard Tour card at a particular Tour card reader. If a guard is late at swiping, or misses swiping a card reader along the tour, it is automatically assumed that the guard may have run into some kind of troble and an alert will be activated, informing other security personnel. Guard Touring is an additional security feature involving the close monitoring of guard patrol movement through their assigned routes in security areas. During a Guard Tour, patrolling guards swipe their Guard Tour cards at specific card readers along their tour, which register on the security interface. Each Guard Tour has a strict schedule, with a list of periods during which the patrolling guard must swipe the Guard Tour card at a particular Tour card reader. If a guard is late at swiping, or misses swiping a card reader along the tour, it is automatically assumed that the guard may have run into some kind of troble and an alert will be activated, informing other security personnel. |
| ID Card Maker |
 Design and create your own unique caed layout. Cards may also be optionally created with a photo of it's assigned cardholder printed onto the card. This photo can be acquired easily using a digital video camera linked to the ID Card Maker Badging System. ID cards provides the visual identification of personnel in your building. Design and create your own unique caed layout. Cards may also be optionally created with a photo of it's assigned cardholder printed onto the card. This photo can be acquired easily using a digital video camera linked to the ID Card Maker Badging System. ID cards provides the visual identification of personnel in your building. |
| Mobile Alert GSM |
 Mobile Alert GSM enables the instant sending of selected events to registered personnel(s) via a GSM (Global System for Mobile communication) handset in the form of SMS (Short Message Service) within the Matrix V System's boundary. Mobile Alert GSM enables the instant sending of selected events to registered personnel(s) via a GSM (Global System for Mobile communication) handset in the form of SMS (Short Message Service) within the Matrix V System's boundary. |
| It also allows authorised personnel(s) to operate a limited number of Door Access Control and Alarm Monitoring Functions by using their mobile phones through SMS. |
| CCTV Interfacer |
 CCTV Remote Cameras may be logically linked to particular security devices, such as card readers. Should an alarm originate from that security device, footage from the linked camera can be fed directly to your computer screen through the Matrix V software to aid security personnel in assessing the situation. Also, event-triggered recording allows a video recorder to automatically record footage from CCTV cameras whenever a system event occurs. CCTV Remote Cameras may be logically linked to particular security devices, such as card readers. Should an alarm originate from that security device, footage from the linked camera can be fed directly to your computer screen through the Matrix V software to aid security personnel in assessing the situation. Also, event-triggered recording allows a video recorder to automatically record footage from CCTV cameras whenever a system event occurs. |
| Facility Manager |
 Facility manager is used to maintain and manage rooms (meeting rooms, function halls), facilities (sports, recreational) and control the access these different areas for predefined groups of people in multi-room and area facilities. The administrator will be able to control, Access & duration for any of the facility is booked for. Facility manager helps the administrator or booking slips and have an overview of all events in the facility to prevent double booking and managng events throughout the facility. Facility manager is used to maintain and manage rooms (meeting rooms, function halls), facilities (sports, recreational) and control the access these different areas for predefined groups of people in multi-room and area facilities. The administrator will be able to control, Access & duration for any of the facility is booked for. Facility manager helps the administrator or booking slips and have an overview of all events in the facility to prevent double booking and managng events throughout the facility. |








 US 19026
US 19026  GB 12264
GB 12264  CA 10436
CA 10436  AU 6866
AU 6866  IE 2321
IE 2321  BR 1160
BR 1160  NZ 1112
NZ 1112  MY 1053
MY 1053 

